Threatlocker was founded in 2017, so we can say it stepped into the cybersecurity ring only recently. While experience is certainly valuable in this industry, there are strengths in ‘new blood’ that cannot be ignored. In this review, we’ll take a closer look at its endpoint protection security platform, and see how it fares compared to Kaspersky, Symantec, and other heavy-hitters.
Threatlocker: Plans and pricing
Unfortunately, Threatlocker does not list the pricing for its endpoint security platform on the website. Instead, potential customers are invited to contact the company’s sales department via email, or phone. The good news is that booking a product demo with one of the company’s ‘Cyber Heroes’ is relatively easy, and there is a 30-day free trial that doesn’t require payment data.
Threatlocker: Features
In our “best endpoint security” series, we’ve reviewed almost all platforms worth a dime and we can tell you straight away - Threatlocker’s array of features is nothing short of impressive.
Its main product page does a great job providing an overview of different features, as well as displaying some of the more basic ones such as app black and whitelisting. What really caught our eye, though, is the ‘Ringfencing’ feature, which allows you to set boundaries for how apps interact with each other.
Sadly, there is no dedicated firewall for clients, but it does have something called 'Dynamic Network Control'. This is a feature that allows IT teams to regulate traffic, or open ports for authorized apps only. It uses dynamic Access Control Lists (ACL), or agent authentications.
According to Threatlocker, this is a security gap that’s often overlooked in endpoint security platforms, and that can often spell disaster if a malicious device infiltrates the network. Rightly so!
The platform’s policy engine is also quite advanced, and can be used as a firewall, to restrict what apps can do. Threatlocker refers to 'Allowlisting' as a way to control the software, scripts, executables, and libraries running on the endpoints and servers. The 'Allow List' can be exclusive, too, blocking any apps that aren’t on it.
There is also an option to set time-based policies, allowing apps to perform certain functions only at a pre-set time of day.
Threatlocker claims customer support is always available, either via phone or the main portal. It also says it “strives” to answer every call within 30 seconds, and solve every issue “on the same call”, within minutes.
Threatlocker: Setup
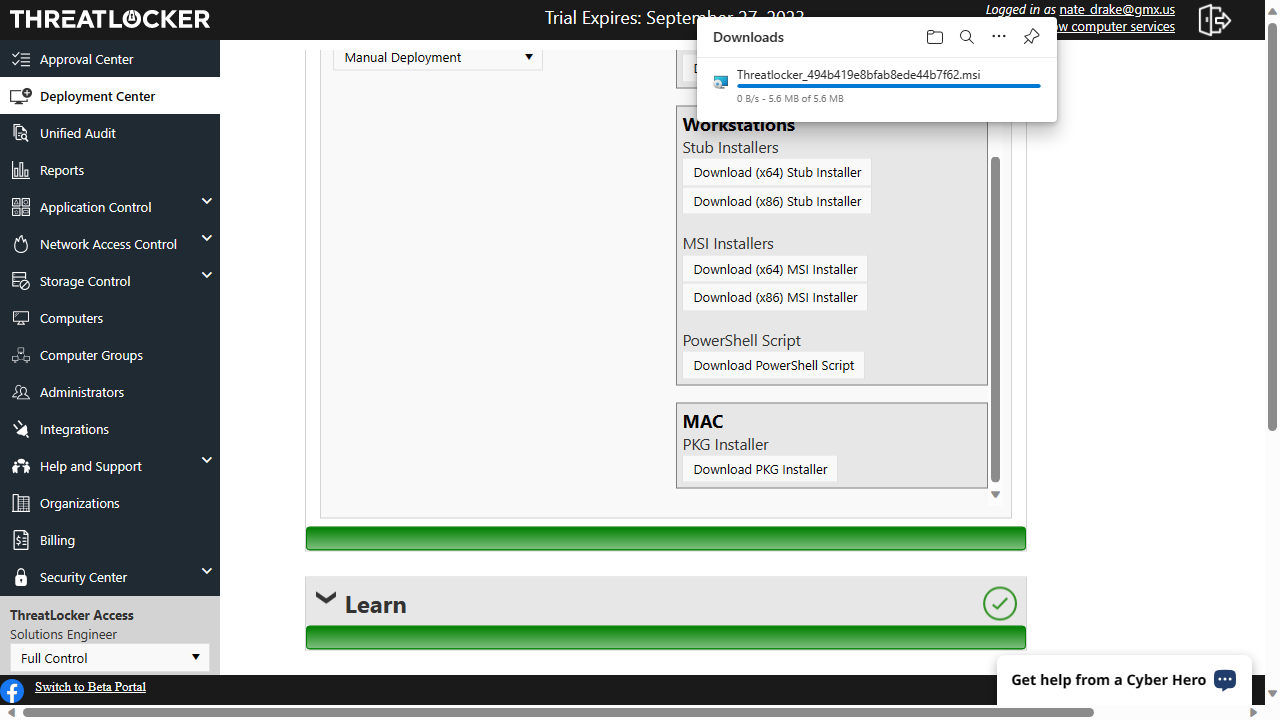
If you go for a trial (as we did), you’ll be asked company and contact details. After that, you can log into the Threatlocker portal, and move over to the ‘Deployment Center’ to install the agent software.
There are multiple ways of doing this, including RMM (Remote Monitoring & Management), software deployment tool, Active Directory and Power Shell. We chose the manual installation using the Windows installer. There's an MSI version but we opted instead for the tiny 'stub' utility, which Threatlocker advises will install the latest version of the ThreatLocker Agent.
Windows (Servers and Workstations) and macOS are both supported. Unfortunately, we couldn’t find Linux or mobile devices mentioned anywhere. However, at press time, Threatlocker did have a job posting for a kernel software developer with experience in Linux, which could mean the platform might be supported in the future.
Threatlocker: Interface
In contrast to Threatlocker’s features, the main interface was somewhat rough around the edges. At times, it felt more like editing a database, rather than working in an online portal.
Still, the left-hand pane was well-designed, with expanding sections. For example, expanding 'Application Control' lists choices such as 'Policies', 'Permitted Applications', 'Applications' and 'Tags'.
What we felt the platform really lacked was a typical dashboard, a place where you can see a quick heads-up of device status, threat blocks, and so on. A few pie charts and other infographics would have been helpful, as well.
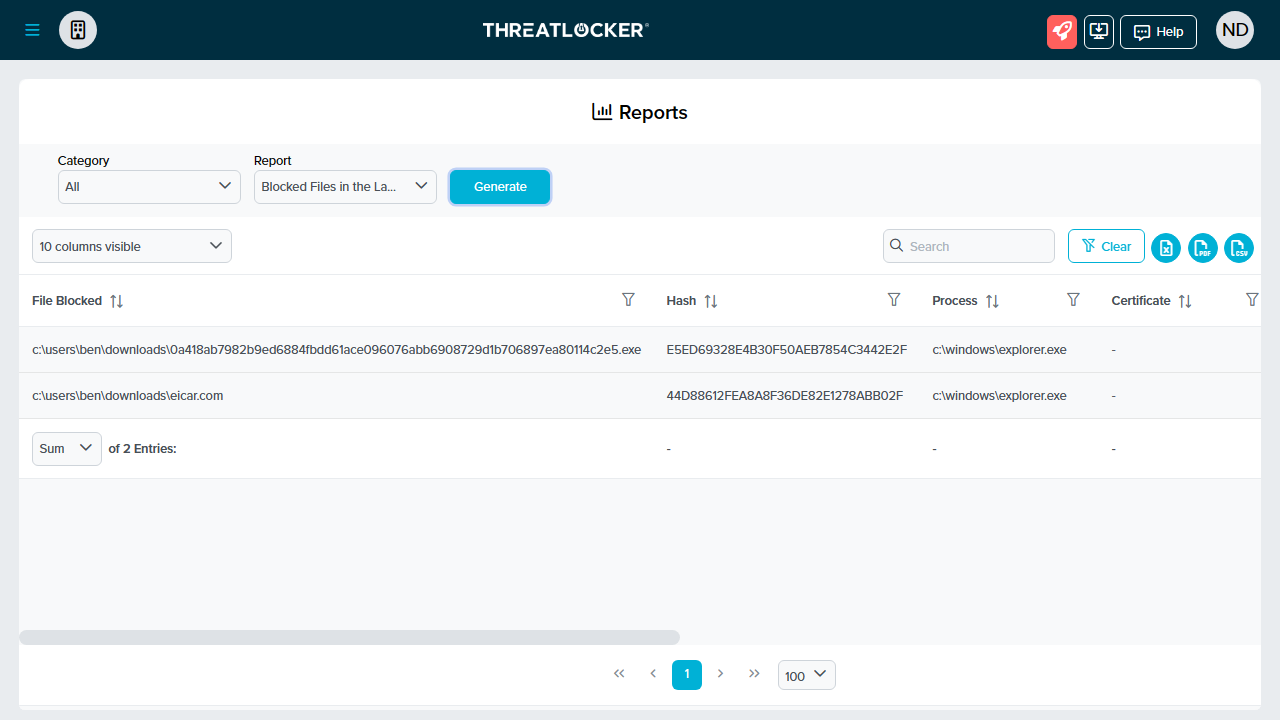
There is a feature to generate reports, where you can build out any amount of data (for example, blocked files in the last 24 hours), but these appear in a spreadsheet-like format. So, be prepared for some clicking and dragging in order to view all the information.
That being said, there is something called the “Beta” portal, which has a richer user interface (UI). You still won’t get the classic dashboard, but it’s easier to see and use all the different options. The left hand pane has also been replaced with a dropdown menu.
We’re still waiting for the Threatlocker Agent to get the 'Beta treatment' so you’ll have to dig through the spreadsheet style to see blocked files.
Threatlocker: Performance
Reviewing Threatlocker is something of an emotional roller coaster. The features were exciting, but the interface was somewhat disappointing. The performance, yet again, got our hopes up. We test all the platforms the same way: with a fake virus, an actual virus, and then we take a look at the logs.
Courtesy of EICAR, we tried to download a fake computer virus, through Microsoft Edge. On our first attempt, we couldn’t extract the file because the permissions were changed. Then we tried to download it uncompressed, but once again, Threatlocker Agent blocked it. This time, we also got a pop-up notifying us of the activity. Interestingly, the agent does include a 'Request Access' option, which may be useful if an endpoint user wants to request permission to run a legitimate program.
We then tried to download and run an actual virus and were stopped in our tracks once again.
Lastly, we logged into the cloud console to check the logs. We used Threatlocker’s beta cloud console and saw the full file names displayed, without any fine tuning via the mouse.
Threatlocker: Final verdict
We’ll take an unrefined interface with a powerful platform, over a fancy-looking dashboard that crumbles under pressure any day. We have to say - it’s rather unfair that Threatlocker is rarely mentioned in the same sentence with heavy-hitters such as Malwarebytes, despite stellar performance.
It is easy to register and install. It has great customer support. It works well, and can easily be fine-tuned.
While we do have a few objections (no dedicated firewall, lack of a graphically-rich agent, no support for mobile), they take away almost nothing from the overall impression.







