
Hackers are now using a combination of malicious apps and brand impersonation to steal the passwords and other sensitive data of unsuspecting Android users.
As reported by The Hacker News, a new malware campaign has been spotted online in which malicious Android apps pose as Google, Instagram, Snapchat, WhatsApp, X and other popular online services in a bid to harvest contacts, text messages, call logs and of course, passwords from vulnerable Android phones.
Although security researchers at SonicWall’s Capture Labs team know quite a bit about this new campaign so far, they aren’t quite sure how the malicious apps used in it end up on the best Android phones. However, these fake apps could be spread on phishing sites, through emails or text messages or they may even come bundled with pirated software.
While we’ll likely learn more regarding the intricacies of this campaign and the hackers behind it once SonicWall does, in the meantime, here’s everything you need to know to avoid getting a nasty malware infection on your own Android phone as the result of a malicious app.
From a fake app to fake login pages
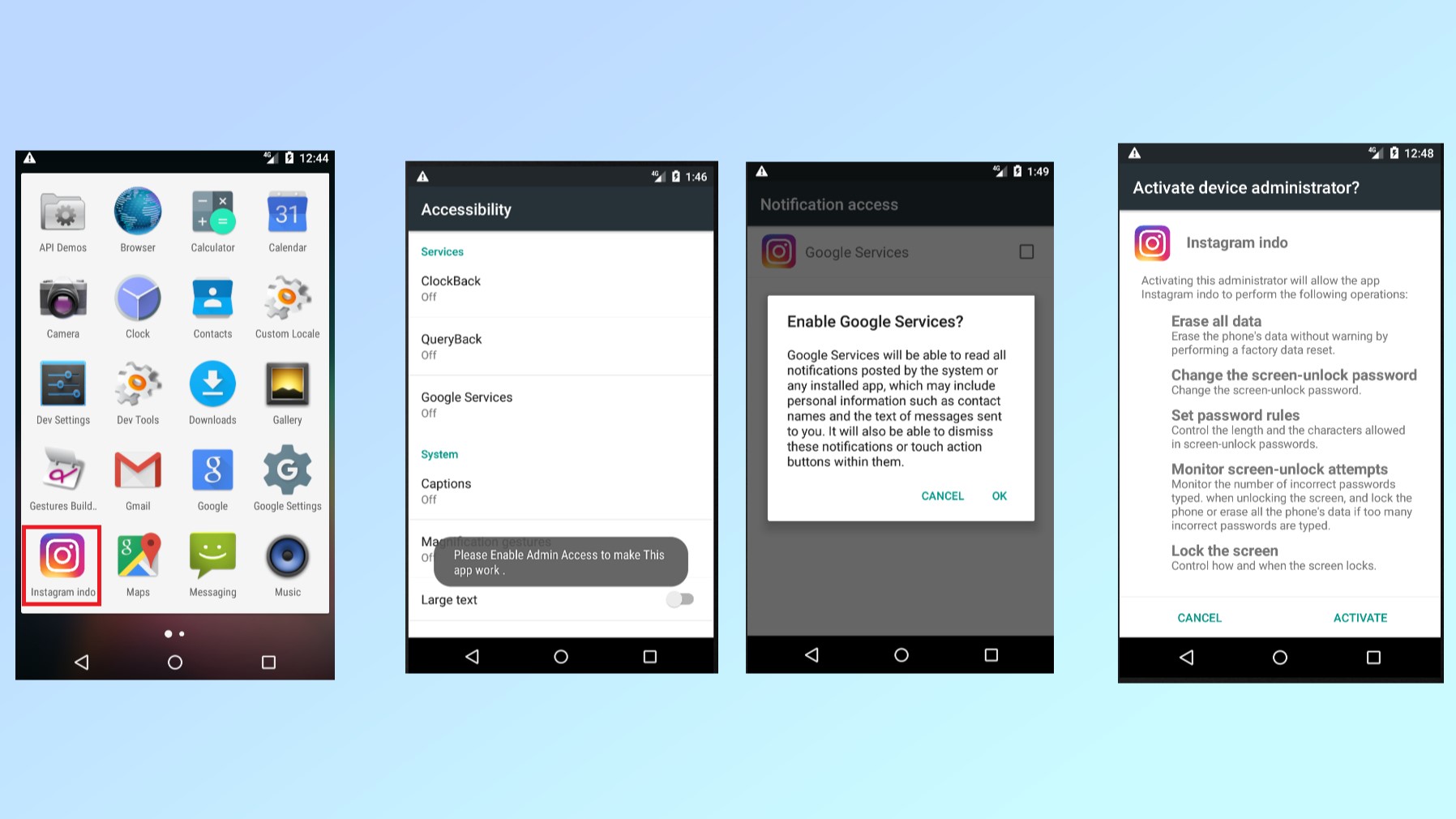
According to a blog post from SonicWall, once the malicious app used to distribute this malware is installed on a victim’s phone, it then uses famous Android app icons from popular apps and online services to hide in plain sight.
When the malicious app is opened for the first time which could easily happen by mistake as it’s impersonating another app, it requests access to two permissions: Android Accessibility Service and Device Admin Permission. If a potential victim grants the app access to these sensitive permissions, it can then take control over their phone and steal sensitive data from it without their knowledge.
The malicious app in question then establishes a connection with a hacker-controlled command and control (C&C) server from which it receives additional instructions. For instance, the malicious app can be used to read messages, read call logs, access notification data, send messages and worst of all, open malicious websites in a victim’s browser for the purpose of phishing.
Essentially, the way in which this malicious app and the malware it contains harvest credentials from victims is by taking them to fake login pages for sites such as Instagram, PayPal, Netflix, Microsoft, WordPress, LinkedIn, ProtonMail, Yahoo and more. They are then prompted to enter their username and password which is stored and then relayed back to the hackers behind this campaign.
From there, they can then take over their online accounts and commit fraud or possibly even identity theft if enough of their sensitive, personal information is contained in one of these services. For instance, if they got a victim’s Microsoft credentials and they use OneDrive to store copies of their driver’s license, passport or even their Social Security number (a terrible idea but some people still do), the hackers could cause some serious trouble.
How to stay safe from Android malware

Since we aren’t entirely sure how this particular malware-filled app is being spread, the best I can do is to give you some overall guidance when it comes to protecting yourself from Android malware.
Google has taken a lot of precautions over the years to significantly decrease the chances of malicious apps ending up on Play Store. However, you still need to be careful when downloading any new app onto your Android phone. You want to check an app’s ratings, reviews and if possible, look for a video review online so that you can see the app in question.
Normally with malicious apps though, they are often sideloaded onto a victim’s smartphone. Surprisingly, this is often done by the victim themselves after being coerced into doing so by a hacker, scammer or some other type of cybercriminal. This is why you need to be extremely wary when someone tells you to install an app in either a text message, email or on social media. If the app isn’t available on a first party app store and needs to be downloaded as an APK file and then installed manually, this is a big red flag and you should avoid it at all costs.
To prevent malicious apps from being installed on your Android phone in the first place, you want to make sure that Google Play Protect is enabled as this pre-installed security app scans all of your existing apps and any new ones you download for malware. If you want to be extra careful though, you should also consider running one of the best Android antivirus apps alongside it.
We may not learn more about this particular campaign but at least now, you know that malicious apps can change their icons to hide in plain sight. Sometimes they do this by pretending to be system apps like contacts or settings or in this case, by impersonating popular apps using their logos and names. Since campaigns like this one can be so effective though, we likely won’t see hackers drop this tactic from their arsenal anytime soon.







