Hackers are targeting victims with fake broken Google Meet calls in an attempt to infect them with malware and thus grab their sensitive information, experts have warned.
A report from cybersecurity researchers Sekoia claim the campaign is a new variant of the previously-observed ClickFix attack.
ClickFix victims are shown a fake error page (for example, a browser that is outdated and thus unable to open a certain website) and then offered a fix (a ‘patch’, or a ‘version upgrade’). If the victims don’t realize the ruse and download the ‘fix’, they end up infecting their endpoints with different malware.
StealC and Rhadamanthys
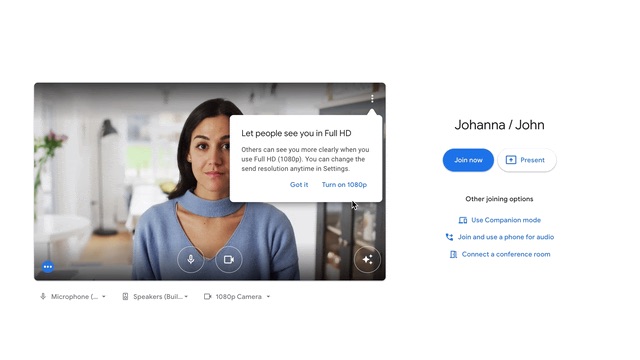
In this instance, Sekoia’s researchers found several websites pretending to be Google Meet video conferencing landing pages.
People that open these websites are shown an error regarding their microphone or camera. The offered ‘fix’ is a PowerShell code, copied to the clipboard, which runs in the Windows Command Prompt.
This code ultimately deploys either the StealC infostealer, or Rhadamanthys. For macOS, which is also targeted, the attackers are dropping the AMOS Stealer as a .DMG file called “Launcher_v194”.
The threat actors in this campaign are called the Slavic Nation Empire (SNE) and Scamquerteo, apparently sub-groups of other threat actors named Marko Polo and CryptoLove, respectively.
Besides Google Meet, Sekoia has found Zoom, PDF readers, fake video games (Lunacy, Calipso, Battleforge, Ragon), web3 browsers and projects (NGT Studio), and messenger apps (Nortex) being abused for the same purpose.
The attack most likely starts with a phishing email, and targets mostly transport and logistics firms.
Via BleepingComputer
More from TechRadar Pro
- This new phishing attack uses a sneaky infostealer to cause maximum damage
- Here's a list of the best firewalls today
- These are the best business VPNs







