
New Zealand-based cyber security experts at CyberCX have detailed and demonstrated an alarmingly simple way to consistently access older BIOS-locked laptops. In the linked blog post, and video demo, an exec at the firm detailed how to short some EEPROM chip pins with a simple screwdriver to access a fully-unlocked BIOS. Then all it took was a quick poke around the BIOS settings screen to disable any BIOS password altogether.
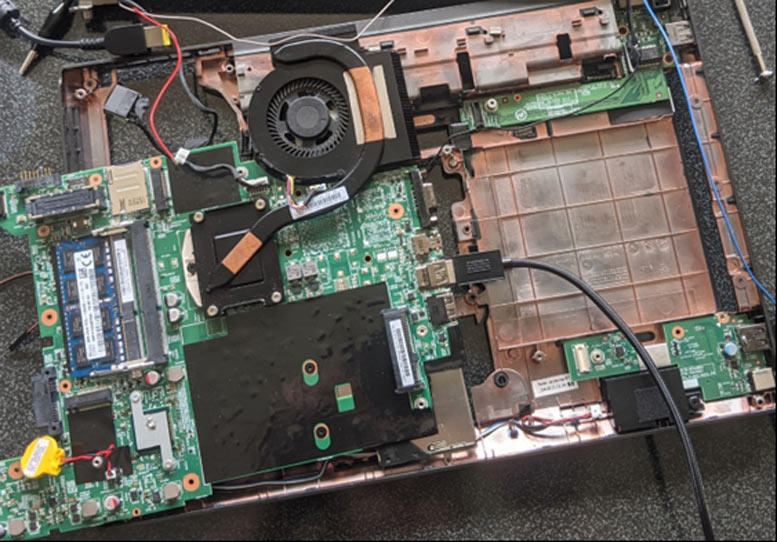
Before we go further, it is worth pointing out that CyberCX's BIOS password bypass demonstration was done on several Lenovo laptops that it had retired from service. The blog shows that the easily reproducible bypass is viable on the Lenovo ThinkPad L440 (launched Q4 2013) and the Lenovo ThinkPad X230 (launched Q3 2012). Other laptop and desktop models and brands that have a separate EEPROM chip where passwords are stored may be similarly vulnerable.

Some of you will know that there are quite a lot of good used laptops sold for spares as they are practically disabled from re-use due to a BIOS lock in place. Individual owners or organizations may have neglected to document these passwords, forgotten them, or whatever - but the systems, which are also usually stripped of their HDDs and/or SSDs, aren't as valuable on the used market as they could be. CyberCX pondered over its old IT equipment that had been password locked and wondered about trying to gain full access to the hardware again to use it as spares or testing machines.
From reading various documentation and research articles, CyberCX knew that it needed to follow the following process on its BIOS-locked Lenovo laptops:
- Locate the correct EEPROM chip.
- Locate the SCL and SDA pins.
- Short the SCL and SDA pins at the right time.

Checking likely looking chips on the mainboard and looking up series numbers eventually lead to being able to target the correct EEPROM. In the case of the ThinkPad L440, the chip is marked L08-1 X (this may not always be the case).
An embedded video in the CyberCX blog post shows just how easy this 'hack' is to do. Shorting the L08-1 X chip pins requires something as simple as a screwdriver tip being held between two of the chip legs. Then, once you enter the BIOS, you should find that all configuration options are open to be changed. There is said to be some timing needed, but the timing isn't so tight, so there is some latitude. You can watch the video for a bit of 'technique.'
CyberCX includes some quite in-depth analysis of how its BIOS hack works and explains that you can't just short the EEPROM chips straight away as you turn the machine on (hence the need for timing).
Some readers may be wondering about their own laptops or BIOS-locked machines they have seen on eBay and so on. CyberCX says that some modern machines with the BIOS and EEPROM packages in one Surface Mount Device (SMD) would be more difficult to hack in this way, requiring an "off-chip attack." The cyber security firm also says that some motherboard and system makers do indeed already use an integrated SMD. Those particularly worried about their data, rather than their system, should implement "full disk encryption [to] prevent an attacker from obtaining data from the laptop’s drive," says the security outfit.
CyberCX hints it will continue the above research. Perhaps it will look into being able to read the BIOS password in plaintext from the EEPROM, or check the viability of its screwdriver hack across more machines.







