
- Microsoft has spotted a new phishing attack vector in the wild
- Storm-2372 is stealing access tokens through Microsoft Teams
- The group has been linked to Russia with medium confidence
A new phishing campaign has been spotted using ‘device code phishing’ through Microsoft Teams to target governments, NGOs, and other industries across Europe, North America, Africa, and the Middle East.
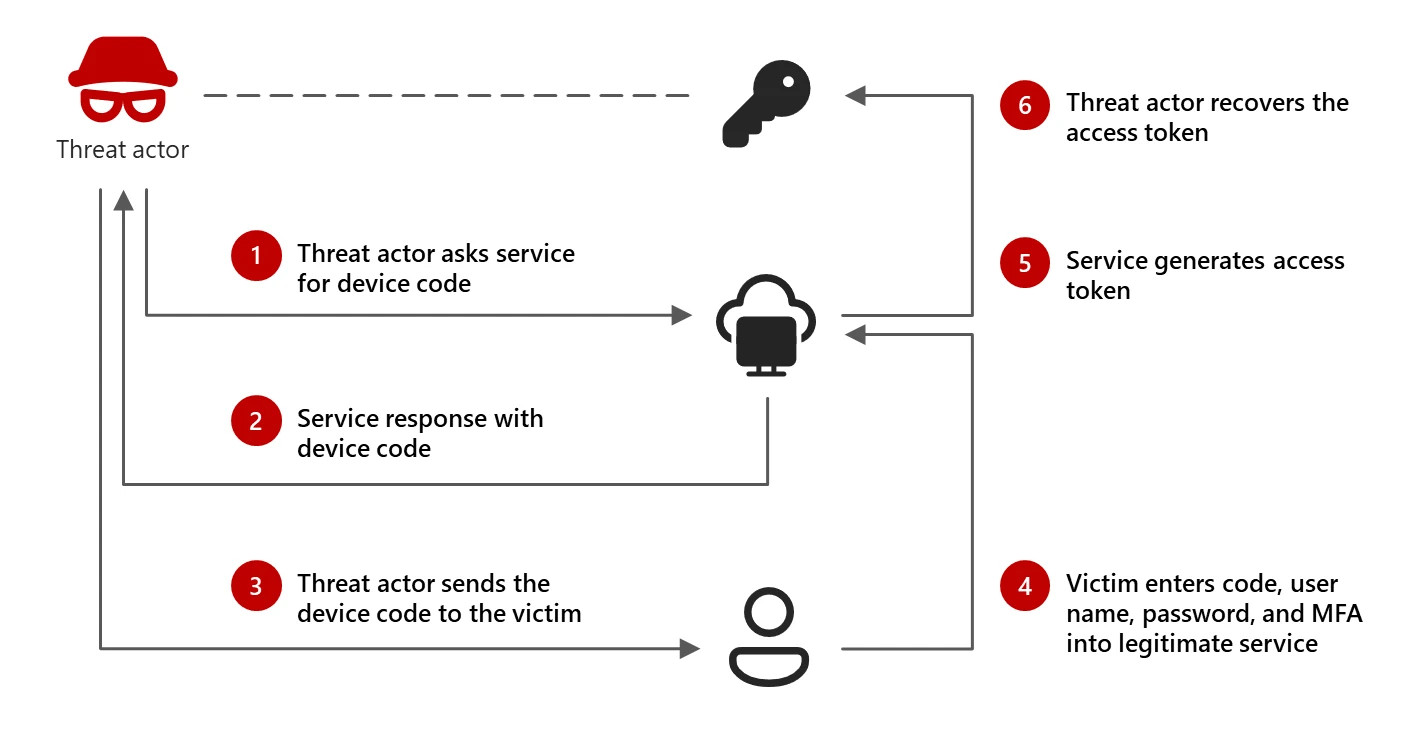
The attack, spotted by Microsoft itself, leverages Teams video conferencing meeting invitations which prompt the victim to enter a device code generated by the attacker which results in the victim handing over valid access tokens, giving the attacker access to victims emails and sensitive data.
Microsoft assesses with a medium level of confidence that the group, tracked as Storm-2372, is acting in line with Russian tactics and interests.
Data theft and lateral movement
Microsoft says the threat actor would first build up a rapport with the victim through messaging services such as WhatsApp, Signal, and Microsoft Teams, positioning themselves as an important figure within the victim’s industry. The attacker then invites the victim to an online meeting, where the victim is prompted to complete a device code authentication request.
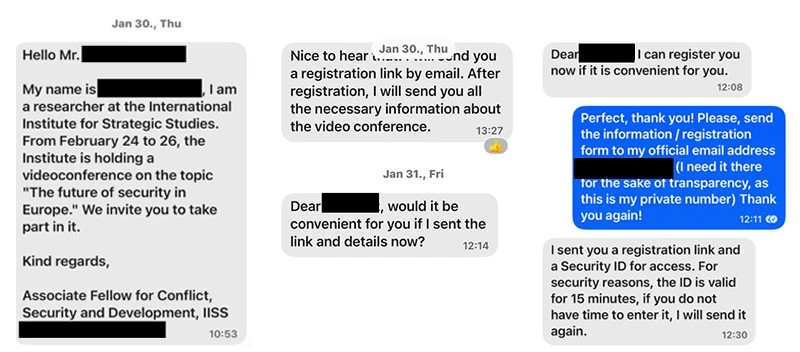
The actor will generate a legitimate device code authentication request, and then send the code to the victim. The victim enters the code into the legitimate authentication service page which allows the attacker to capture access and refresh tokens to maintain control over the account.
From there, the attacker will often attempt to move laterally using the valid access tokens, using a keyword search in the messaging service to harvest sensitive data including usernames and passwords, as well as data related to the admin, teamviewer, anydesk, credentials, secret, ministry, and gov keywords.
The attacker can also use the compromised account to message or email colleagues with additional phishing messages. Storm-2372 has also been observed using the specific client ID for Microsoft Authentication Broker to request additional tokens that allows the attacker to register their own devices as an authentication device through Entra ID.
In order to protect against the specific attack vector used by Storm-2372, Microsoft recommends:
- Disabling device code flow wherever possible.
- Provide phishing training to all users.
- Revoke access tokens when Storm-2372 activity is suspected using revokeSignInSessions.
- Introduce a sign-in risk-based policy to to block access or force multi-factor authentication for high-risk sign ins.
The full list of defenses and mitigation can be found here.
You might also like
- Take a look at the best password managers
- These are the best authenticator apps
- SonicWall firewalls hit by worrying cyberattack







