
Even though video calls aren’t quite as commonplace as they used to be, millions of people all over the world including myself rely on them when working remotely. As such, they remain a popular target for hackers, and a new malware campaign shows how they can be the perfect lure for unsuspecting PC and Mac users.
As reported by BleepingComputer, the French cybersecurity firm has identified a new ClickFix campaign that uses fake Google Meet pages to trick people into infecting their PCs and Macs with malware.
This isn’t the first time I’ve warned about ClickFix. Back in June, hackers used this social engineering trick to target Google Chrome and Microsoft Word users through fake error messages too. As you can see, it’s quite effective which is why they’ve now started going after Google Meet users. This makes sense, though, as the urgency to join a video call on time is the perfect way to get people to lower their guard.
Here’s everything you need to know about this latest ClickFix campaign along with some tips and tricks on how you can keep your own PC or Mac safe from malware.
From phishing to fake sites to malware

Just like with other malware campaigns, this one uses phishing emails as a means for the hackers behind it to gain a foothold over their victims and their computers.
These phishing emails are quite convincing too as they look like actual Google Meet video call invites. However, if you inspect the URLs for these meeting links, you can tell that something is off. Here are few used in the campaign:
- meet[.]google[.]us-join[.]com
- meet[.]google[.]web-join[.]com
- meet[.]googie[.]com-join[.]us
- meet[.]google[.]cdm-join[.]us
If you’re familiar with Google Meet and use it as often as I do, then you’ll know that “meet.google.com” is the correct URL and that there shouldn’t be anything between the word Google and the .com top level domain.
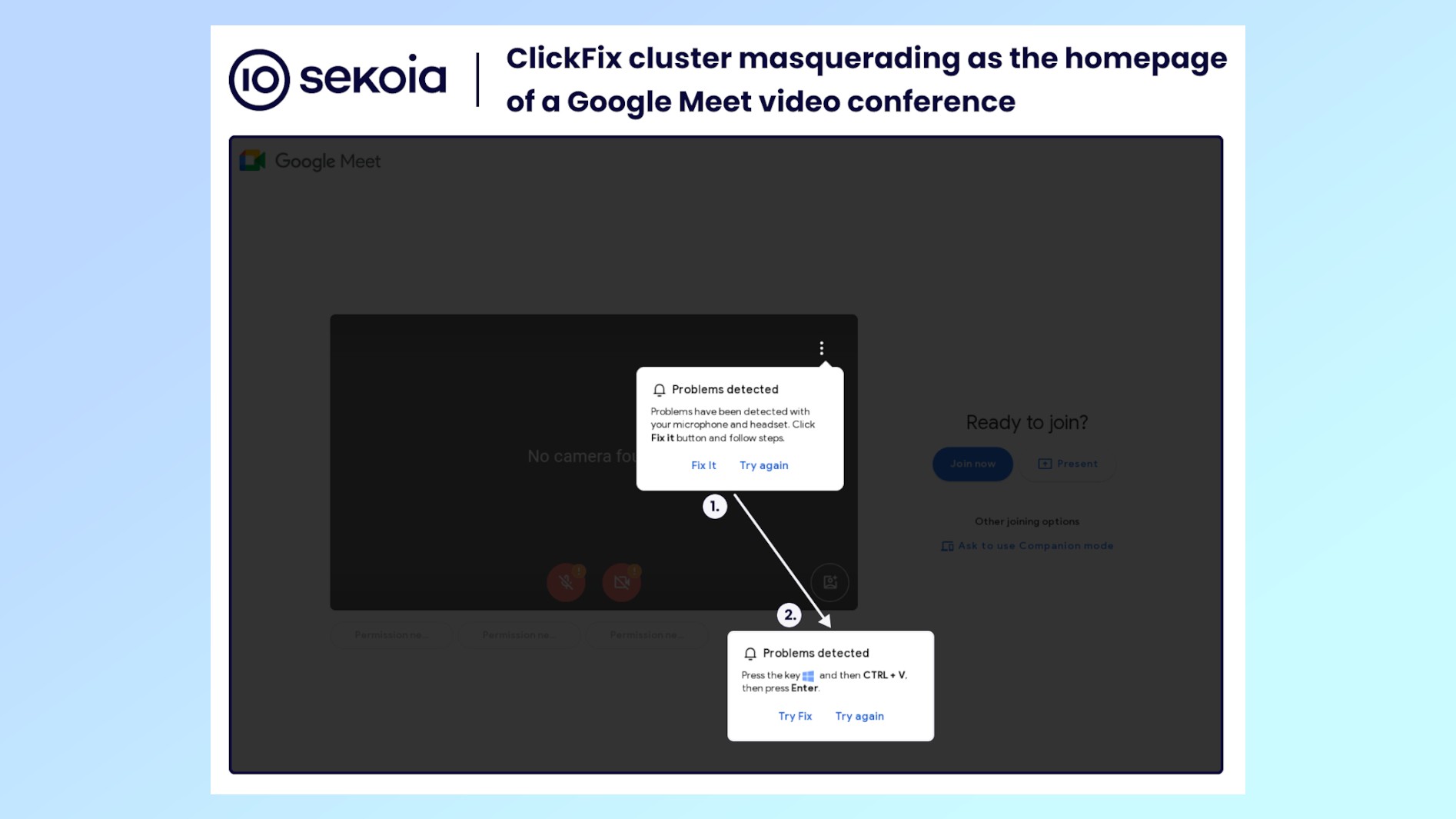
Still, those in a rush or less familiar with Google Meet, might click on one of these fake landing pages. When that happens, they’re presented with a pop-up message warning them of a technical issue — like a microphone or headset issue — that needs to be fixed.
If they click the “Try Fix” button in the error message, a ClickFix infection process begins where PowerShell code from the site is pasted in a Windows prompt that infects their computer with either the Stealc or Rhadamanthys malware. On one of the best MacBooks, the hackers behind this campaign drop the AMOS stealer as a .DMG file named “Launcher_v194” instead.
In its report on the matter, Sekoia’s researchers explain that in addition to Google Meet, they’ve also identified similar ClickFix campaigns that use Zoom, PDF readers, fake video games, web3 browsers and messenger apps as a lure too.
How to keep your PC or Mac safe from malware

For an attack like this, the most important thing you can do is to be extra careful when checking your inbox. You want to look out for emails from unknown senders as well as ones that convey a sense of urgency in order to get you to click on the links or download any attachments they may contain.
From there, you should start inspecting URLs if you don’t already do so. It’s easy to look up a company or a service’s official website and see how their pages look. That way, you can tell whether or not a link is suspicious before you actually click on it.
When it comes to protecting your PC or Mac, you want to ensure you’re using the best antivirus software with your Windows computers and the best Mac antivirus software with your Apple computers. They both come with free, built-in antivirus software in the form of Windows Defender and XProtect but paid antivirus software is usually updated more frequently to keep you safe from all of the latest threats.
ClickFix is a social engineering trick that has been quite successful so far and throughout this year, we’ve seen hackers launch multiple campaigns that use it. As such, this isn’t the type of threat or attack technique that will be going away anytime soon.







