From the theft of 26,000 Kiwisaver customers' data to DDoS attacks on the NZX and two big banks, the Financial Markets Authority is trying to assist the financial sector in fighting back. James Greig asks, is your money next on cyber attackers’ hit list?
Comment: New Zealand’s response to Russia’s war on Ukraine has heightened the risk of cyberattacks on our digital shores – and financial service providers are known to be a prime target.
We’ve already seen an upswing in the size and severity of cyberattacks in recent years: the hacking of a KiwiSaver provider in 2020 and theft of 26,000 of its customers’ information; the NZX going offline for days later that year due to a distributed denial of service (DDoS) attack; and the same happening to two of our big banks’ online services just last year. In some of these cases we, the Financial Markets Authority, worked closely with the entities to respond to the attacks and prioritise customer and investor interests.
Now there’s the very real threat of military cyber campaigns being waged by Russia or its operatives - on top of all the usual malicious actors just trying to make a dishonest buck.
So which of us will be next? Will it be your private details stolen to be traded on the dark web? Or your online accounts made inaccessible?
More to the point, what is your bank, insurer, KiwiSaver provider doing right now to prevent it? Because if there’s one thing that’s almost certain about this year, it’s that cyberattacks will continue.
We need only look to recent statistics to know they are not going away.
Finances a popular target
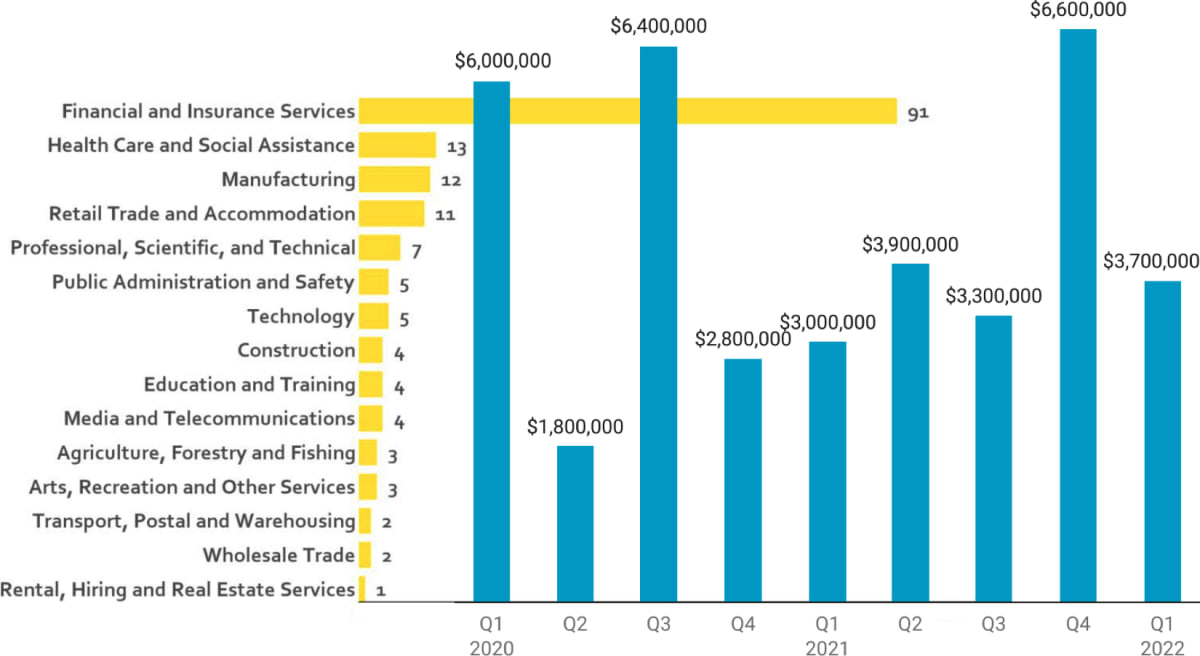
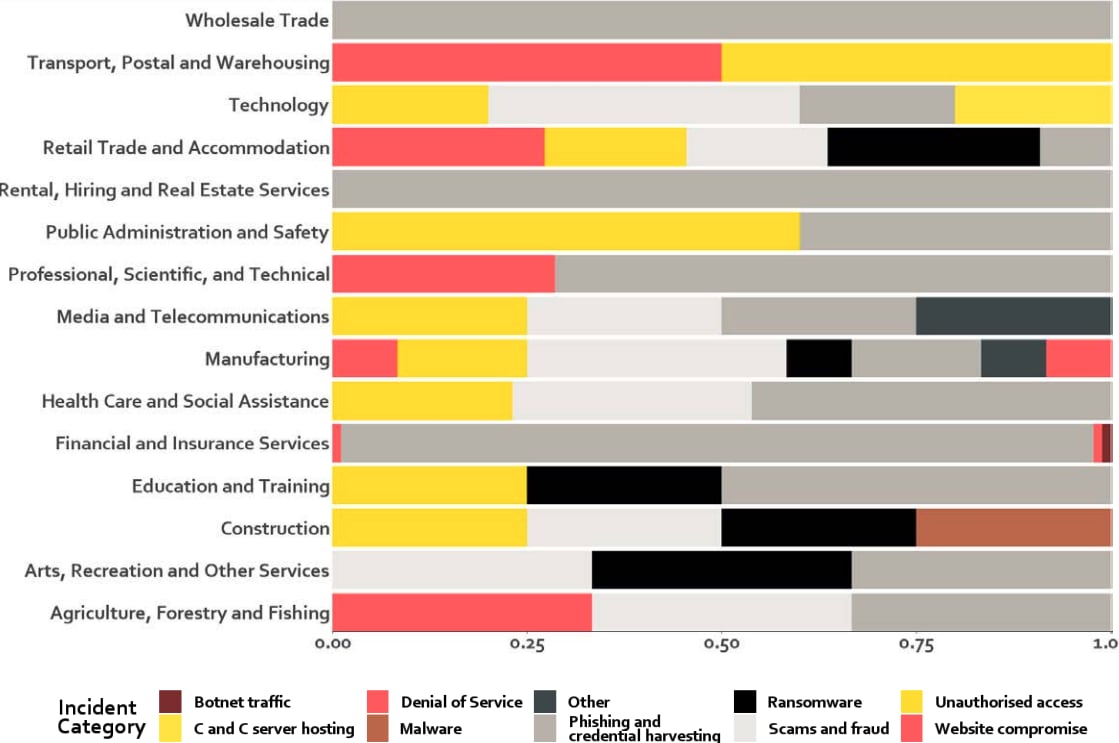
In just the first quarter of this year, 167 cyber incidents affecting New Zealand organisations were reported to CERT NZ, of which over half had targeted the finance and insurance sector alone.
These attacks don’t just harm organisations and their customers, they also erode consumer trust and confidence in our financial services.
It’s unfortunate, but a reality of the modern commercial landscape, that while technology has made financial transactions faster and more accessible, it’s also created new risks.
Such a threat to our collective financial wellbeing demands a commensurate response by the companies, big and small, who are entrusted with our wealth.
That’s why the Financial Markets Authority has just released an information sheet to help the financial sector be more resilient to cyberattacks. It’s our role to ensure the sector meets the minimum standards of their licences when it comes to having IT systems that are secure and reliable, and the information sheet makes it clear what’s expected of them.
Bare minimum security
Just as your contents insurer expects you to have locks on your doors, the FMA also has minimum expectations of financial service providers and their cyber security. These include systems and controls that ensure their security is appropriate to the size and the nature of their business.
For example, no matter how many customers an entity has, they should ideally have what’s called a “Grandfather-Father-Son” backup strategy, where data is stored in cycles, typically monthly-weekly-daily (hence the name).
Firms should also be regularly educating their staff about the risks, because while people can be the biggest strength in detecting threats, they can also be a huge weakness. We all know of someone who has clicked a link to something they shouldn’t have.
Providers should be reviewing their cyber resilience at least annually and remaining vigilant for any unusual activity – reviewing audit logs, system access and transactional behaviour. And they should never assume it couldn’t happen to them, as it definitely could.
A response and recovery plan should be in a provider’s top drawer, so they know how to act in the event of an attack – including reporting it urgently to the relevant regulators, and their customers – and how to resume essential services quickly.
We would certainly expect that customers are returned to the situation they were in as if the incident hadn’t occurred, and that should be done in an appropriate and timely manner.
Investing in cyber resilience
Of course, any financial service provider that is committed to protecting their clients’ money and personal information will look beyond those bare minimum expectations.
Providers should always have an ear out for new threats affecting their industry and look overseas for developments that will eventually arrive here. They may not feel vulnerable now, but new trends can quickly emerge.
Firms should be continually investing in cyber resilience, and recognising it as a necessary fixed cost, equivalent to insurance against events that might cost them much more – including their reputation.
If a provider doesn’t have sufficiently trained in-house staff, they should consider engaging the services of an independent specialist who can help them understand their vulnerabilities, and even conduct penetration testing so the provider knows where to focus resources.
Constantly educating customers should be a priority too: about the importance of regularly changing passwords and having robust cyber protection software; and the risks of sharing their details online. In other words, a provider’s responsibilities don’t end at their shopfront door.
Resilience is not optional
In 2019, the FMA surveyed financial service providers about their cyber resilience. Worryingly, most did not rate themselves highly on their ability to detect and respond to threats. Most expected to improve over the following years – and this was the FMA’s expectation too.
Three years on, we have now heightened our focus on resilience, meaning we will be taking a closer look at providers and checking if their capabilities have indeed improved. That may mean some providers need to consider their action plans and bolster their defences. Cyber threats are constantly evolving – are providers keeping pace?
It’s unfortunate, but a reality of the modern commercial landscape, that while technology has made financial transactions faster and more accessible, it’s also created new risks.
And while we shouldn’t necessarily accept the bad with the good, we certainly should prepare for it, and for the worst-case scenario at that.