
In the 2022 federal budget, Treasurer Josh Frydenberg launched a range of vote-winning initiatives – one of which included a breathtaking A$9.9 billion for cyber security over ten years.
Bundled under the acronym REDSPICE (which stands for resilience, effects, defence, space, intelligence, cyber and enablers), the program is expected to help build Australia’s intelligence and defensive (and offensive) capabilities.
But what does this mean, where is the money coming from and just how offensive are we planning to be?
What’s REDSPICE?
REDSPICE is a program to grow and enhance the intelligence and cyber capabilities of the Australian Signals Directorate (ASD) — the chief agency responsible for foreign signals intelligence, cyber warfare and information security.
Headline figures include 1,900 new recruits and delivering three times more offensive capability within the ASD.
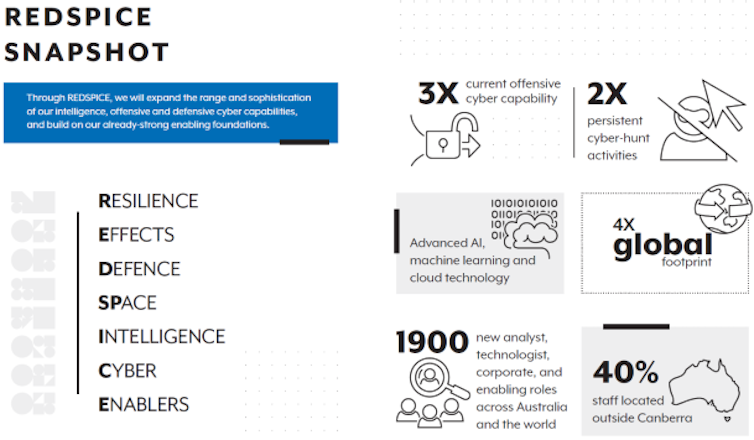
A key justification given for the program is, according to Defence Minister Peter Dutton, the “deteriorating strategic circumstances in our region” and “rapid military expansion, growing coercive behaviour and increased cyber attacks” from Australia’s adversaries.
This was also reinforced in a pre-budget comment from Dutton, who warned of China’s cyber warfare capability to launch “an unprecedented digital onslaught” against Australia.
Potential outcomes
The plans for the program will have effects beyond Canberra. They could see more Australian technologies being made available to our intelligence and defence partners overseas, as well as opportunities for increased data sharing (which is key to fighting against cyber threats).
Further investment in advanced artificial intelligence and machine learning will likely be used to detect attacks earlier than currently possible – potentially allowing automated responses to cyber incidents.
Identifying previously “unseen” attacks is another significant challenge, and using advanced technologies to detect such incidents is essential for a strong defence.
Similarly, a doubling of “cyber-hunt activities” will see an increase in the analysts and automated systems actively looking for vulnerabilities in critical infrastructure. This is essential in protecting the services we depend on day-to-day.
A major attack against our water, electricity, communications, health care or finance services could have devastating consequences – first for the most vulnerable among us, and subsequently for everyone.
All of these technologies will be of value in reducing the large number of threats and incidents seen on a daily basis, and prioritising certain threats so they may be better handled by limited human resources in agencies.
The program will reportedly ensure a distribution of key functions both nationally and internationally, with a focus on building resilience in the “critical capabilities” of the ASD’s operations.
Some new money, but mostly old money
A$10 billion sounds like a significant windfall for our defence and intelligence agencies. However, a closer look indicates the “new” money is perhaps only worth around A$589 million in the first four years.
The majority of the balance comes from redirecting existing defence funding to the ASD.
Also, since the funding is spread over a ten-year period, it will only realise a proportion of the intended outcomes in the next government’s term. In fact, only A$4.2 billion falls within the next four years.
Future governments can always revisit these funding commitments and decide to make changes.
Is Australia ready to be an offensive cyber player?
Offensive cyber is perhaps the inevitable consequence of the increasing levels of cyber threats around the globe.
Not only have we seen global cyber crime increasing, but there is growing evidence of nations being willing to engage in cyber warfare. Recently this has been illustrated through Russia’s cyber attacks against Ukraine.
Australia has had a publicly acknowledged cyber offensive capability for some time. This was even outlined in the government’s April 2016 cyber security strategy (and this was just the first official acknowledgement). It’s likely Australia has had this capability for even longer.
Offensive cyber represents a significantly different approach to a purely defensive or reactive approach. Initiating an attack (or retaliating) is a dangerous endeavour which can have unpredictable consequences.
Launching a highly targeted attack from Australia is certainly possible, but with such attacks we often see consequential damage that affects individuals and systems beyond the target. For example, the NotPetya malware, first identified in 2017, rapidly moved outside of the target country (Ukraine) and had significant financial impact around the world.
In the 2016 strategy there was specific reference to the importance of legislative compliance:
Any measure used by Australia in deterring and responding to malicious cyber activities would be consistent with our support for the international rules-based order and our obligations under international law.
But this is largely absent in the (brief) REDSPICE blueprint. Also, due to the covert nature of operations conducted by the ASD, we are effectively being asked to accept Australia operates ethically in the absence of any recorded or published data on operations to date.
Although there have been limited reports of legitimate cyber engagements, a 2016 Address to Parliament by then Prime Minister Malcolm Turnbull referred to offensive attacks conducted by Australia in relation to operations against Islamic State (in partnership with UK and US allies):
While I won’t go into the details of these operations […] they are being used […] they are making a real difference in the military conflict […] all offensive cyber activities in support of the ADF and our allies are subject to the same Rules of Engagement which govern the use of our other military capabilities in Iraq and Syria […]
Will it make a difference?
We all want Australia to be a safe place, so any investment in intelligence and cyber security will be welcomed by most people. That said, it’s worth remembering this battle can never really be won.
Cyber defence is a constant game of cat-and-mouse. One side builds a better weapon, the other builds a better defence, and so it goes. As long as our adversaries are prepared to invest in technologies to infiltrate and damage our critical infrastructure, we will have a continued need to invest in our defences.
The increased focus on offensive initiatives may give us (and our allies) the upper hand for a while, but the cyber world doesn’t stand still. And the pockets of some of our cyber adversaries are also very deep.
Paul Haskell-Dowland does not work for, consult, own shares in or receive funding from any company or organisation that would benefit from this article, and has disclosed no relevant affiliations beyond their academic appointment.
This article was originally published on The Conversation. Read the original article.







