
Cyberattacks are not just a threat to personal data and privacy, but are also an integral part of the toolkit used by state and non-state actors to influence modern conflicts.
In recent years such assaults have been used to influence elections, disrupt critical infrastructure, expose state secrets and spread misinformation.
But what are the motivations and effects of cyber attacks in modern conflicts, and what are the implications for global security in the future?
The strategic goals of cyber warfare
Typically within the context of modern conflicts, cyberattacks are carried out to confuse, disrupt, and demoralize the civilian population and authorities of the target country. They are more or less a psychological operation to figuratively and literally make a conflict hit home.
- Confusion usually takes the form of misinformation, disinformation, and malinformation by spreading content that makes it difficult to get a clear picture of a current conflict or to erode popular support abroad.
- Disruption is the targeting of devices and infrastructure vital to the normal operation of information networks, services and government/military communication, or the targeting of supply chains.
- Demoralization involves targeting the services critical to the day-to-day survival of a civilian population, such as power, electricity, and healthcare.
Last year Google’s Fog of War report, co-written by the Threat Analysis Group (TAG), Mandiant and Trust & Safety, explained the impact of cyber operations and the greater role they play on both sides of the Russia-Ukraine war.
Now, the company has released its follow-up report, 'Tool of First Resort: Israel-Hamas War in Cyber’, co-written by TAG and Madiant, which examines the role of cyber in the Israel-Hamas war.
Cyber as a Tool of First Resort
The report provides several key observations on the use of cyber in the Hamas-Israel war, particularly on the attacks undertaken by Iran and Hamas-linked groups on targets such as Israel, the US, and intra-Palestine groups.
Shane Huntley, Senior Director of TAG, initially outlined that cyber attacks are typically a tool of first resort, in that cyber attacks are, “something that comes early and something that can exist with kinetic attacks or without.”
For example, in the run up to the Russian invasion of Ukraine, many analysts detected a significant uptick in cyber attacks by Russian-linked groups with a particular focus on wiping attacks. These attacks use malware that attempts to remove an organization's ability to function by destroying or preventing access to some or all of their files.
This increase in cyber activity, combined with military exercises along the Russia/Belarus-Ukrainian border, provided a warning of the subsequent invasion and has since been recognized as a signaling of the Kremlin’s motivations prior to the so-called ‘special military operation’.
However, the Hamas-Israel war differs from this norm as, during the run up to the October 7th terrorist attack last year, there was no discernable uptick in Hamas-linked cyber attacks. During the press conference, Sandra Joyce, VP, Threat Intelligence at Mandiant, assessed that this may have been intentional.
Joyce explains that Hamas may have deliberately maintained their cyber operations at a normal level as the “[potential] operational security risks from a cyber operation really outweighed the assessed potential benefit.”
This isn’t to say that Israel has not been subjected to any cyber attacks, as Iran has been building its cyber capabilities since as far back as 2012 in its targeting of Israel, the US, and other western countries.
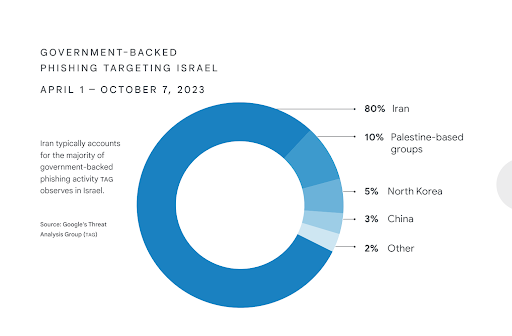
TAG Threat Intelligence Analyst, Kristen Dennesen, pointed out that in the six months preceding the October 7th attack Iran accounted for “80% of the government-backed phishing activity that we saw targeting Israel.”
The report asserts that typically Hamas-linked groups have relied on simplistic but effective tactics, techniques and procedures (TTP) to carry out its cyber campaigns. However, Dennesen highlighted a particular attack attributed to the BlackAtom group which showed an elaborate use of social engineering.
The BlackAtom group contacted Israeli programmers with job offers advertising increased wages if they could complete a Visual Studio coding proficiency task, which was downloaded from a GitHub repository controlled by BlackAtom. The task contained a ZIP file which, when extracted, executed the SYSJOKER malware inside.
TTP refinement during the Hamas-Israel war
In the immediate aftermath of the October 7th attacks, Hamas-linked groups sought to abuse the rush of civilian support by launching demoralizing cyber campaigns against the Israeli population.
One of the most poignant examples of this was the GreatRift groups’ use of a website masquerading as an Israeli hospital that distributed malware through blood-donation documents. Furthermore, Hamas-linked groups also attempted to disrupt the Israeli government, along with defense contractors and data hosting services, using the 'BiBi' wiper malware.

One particular adaptation of TTPs that Dennesen points out is the increased use of mobile spyware immediately following the October 7th attack. Israel’s ground invasion was met with a surge in the intensity of rocket attacks from groups supportive of Hamas, such as the Houthis and Hezbollah.
Hamas-linked groups took advantage of the Israeli population's surge to download apps such as Red Alert, which provides emergency alerts on incoming rocket attacks. The Hamas-linked threat actors created an identical app which when downloaded would install malware and spyware on the victims device.
Iran-backed threat actors have also used Android-based malware as part of intelligence gathering operations targeting Israeli devices. The spyware employed, known as Mythdroid, was likely distributed using social engineering campaigns and malicious Israeli-themed websites.
Retribution from Israeli actors
John Hultquist, Chief Analyst, Mandiant, pointed out that in the immediate aftermath of the October 7th attacks, the threat actor known as Predatory Sparrow distributed messaging that they were going to carry out retribution against Hamas and its allies.
There have been a number of notable cyber disruptions to Iranian infrastructure since then, with one attack affecting 70% of Iran's petrol stations last December being claimed by and attributed to Predatory Sparrow.
While this actor has been active since as early as October 2021, the intensity and effects of the attacks attributed to Predatory Sparrow by Iran have increased.
What to expect in 2024
Hamas-linked groups’ capabilities to launch cyber attacks and social engineering campaigns has been disrupted in the wake of the war with Israel, but Joyce points out, “that Hamas cyber activity will eventually resume, so it [will] be focused on espionage for intelligence gathering on these intra-Palestinian affairs, Israel, the United States and other regional players in the Middle East.”
Joyce also pointed out the importance of cyber resilience at home as, “whether they're prepared or not, whether they know it or not, and whether they like it or not” the private sector is a target to threat actors on a global scale.
With several key elections occurring not only in the US, but also in the UK, India, and Russia, there is the expectation that key threat-actors will focus on election interference and misinformation campaigns.
More from TechRadar Pro
- Key US government body says it might have been breached, with thousands of employees affected
- Boost your security with our guide to the best firewall software
- Take a look at our rankings of the best endpoint protection software







